Vulnerability: Page 3
-
CISA, Microsoft update guidance on Exchange Server vulnerability
Officials reiterated their belief that hackers were not exploiting the flaw, but nonetheless urged users to immediately check their systems.
By David Jones • Aug. 13, 2025 -
Xerox patches critical vulnerability in FreeFlow Core application
Researchers at Horizon3.ai discovered the flaw after flagging unusual behavior in a customer environment.
By David Jones • Updated Aug. 13, 2025 -
Citrix NetScaler flaws lead to critical infrastructure breaches
Dutch authorities said hackers penetrated several critical infrastructure providers, in a warning sign for vulnerable organizations elsewhere.
By Eric Geller • Updated Aug. 12, 2025 -
Research shows AI agents are highly vulnerable to hijacking attacks
Experts from Zenity Labs demonstrated how attackers could exploit widely deployed AI technologies for data theft and manipulation.
By David Jones • Aug. 11, 2025 -
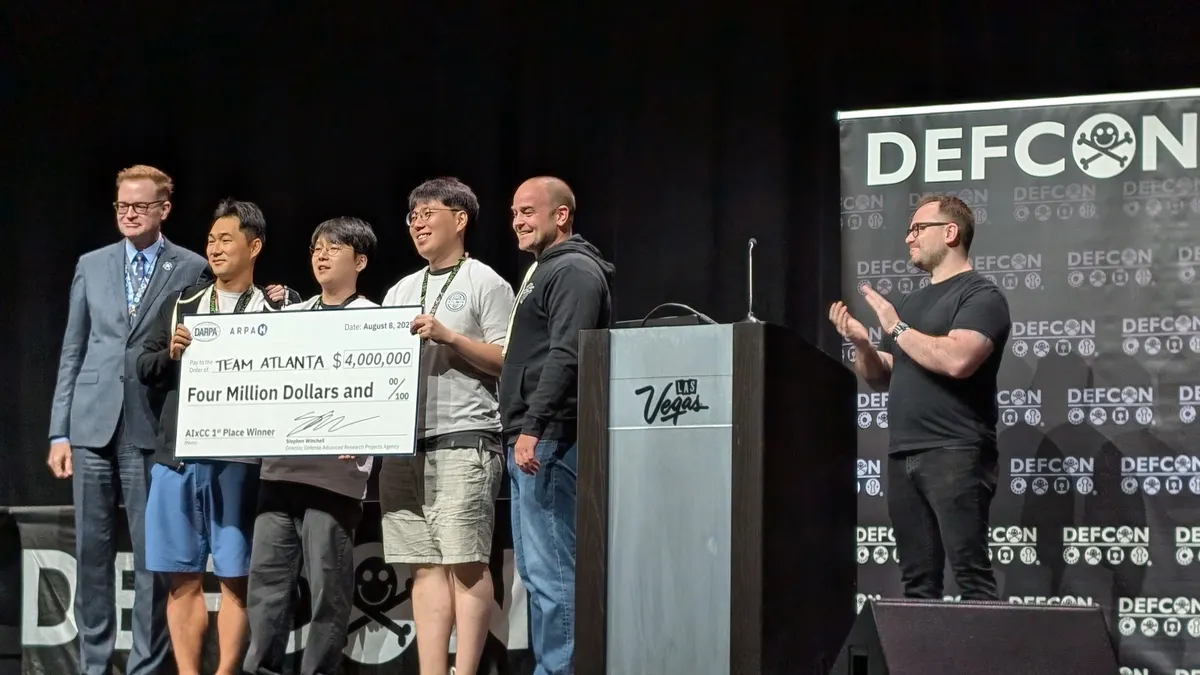
DARPA touts value of AI-powered vulnerability detection as it announces competition winners
The U.S. military research agency hopes to foster a new ecosystem of autonomous vulnerability remediation.
By Eric Geller • Aug. 8, 2025 -
Financially motivated cluster a key player in ToolShell exploitation
Researchers from Palo Alto Networks detail ransomware deployment and malicious backdoors in a campaign against Microsoft SharePoint users.
By David Jones • Aug. 8, 2025 -
SonicWall says recent attack wave involved previously disclosed flaw, not zero-day
The company said it had linked recent hacks to customers’ use of legacy credentials when migrating from Gen 6 to Gen 7 firewalls.
By David Jones • Aug. 7, 2025 -
CISA, Microsoft warn about new Microsoft Exchange server vulnerability
The flaw could enable a hacker to perform a “total domain compromise” on affected systems, CISA said.
By David Jones • Updated Aug. 7, 2025 -
Top US energy companies frequently exposed to critical security flaws
A report from security firm SixMap shows that a large number of energy companies use equipment with vulnerabilities that are located on potentially exposed ports.
By David Jones • Aug. 6, 2025 -
SonicWall investigating possible zero-day related to firewall attacks
Researchers recently warned about a surge in Akira ransomware attacks linked to a potential SonicWall vulnerability.
By David Jones • Aug. 5, 2025 -
AI is helping hackers automate and customize cyberattacks
CrowdStrike’s annual cyber-threat-hunting report reveals the double threat that AI poses to many businesses.
By Eric Geller • Aug. 4, 2025 -
Ransomware spike linked to potential zero-day flaw in SonicWall devices
Researchers say hackers using the Akira ransomware strain may be exploiting the vulnerability en masse.
By David Jones • Updated Aug. 4, 2025 -
Palo Alto Networks investigating ransomware threat related to SharePoint exploitation
Researchers said an unidentified hacker demanded a ransom after an intrusion linked to the SharePoint flaw.
By David Jones • Aug. 1, 2025 -
DOJ reaches $9.8 million settlement with Illumina over cyber whistleblower claims
The U.S. alleged the company knowingly sold genetic-sequencing systems with software vulnerabilities to federal agencies.
By David Jones • Updated Aug. 1, 2025 -
‘Shadow AI’ increases cost of data breaches, report finds
Companies are failing to protect their AI tools from compromise, often leading to more extensive data breaches, according to new data from IBM.
By Eric Geller • July 30, 2025 -
Ransomware attacks against oil and gas firms surge
Manufacturing remains the No. 1 ransomware target, new data from Zscaler shows.
By Eric Geller • July 29, 2025 -
Research shows LLMs can conduct sophisticated attacks without humans
The project, launched by Carnegie Mellon in collaboration with Anthropic, simulated the 2017 Equifax data breach.
By David Jones • July 28, 2025 -
Treasury sanctions North Koreans involved in IT-worker schemes
Authorities also charged several of the indicted people with attempting to evade U.S. sanctions on North Korea.
By Eric Geller • July 25, 2025 -
What we know about the Microsoft SharePoint attacks
State-linked hackers and ransomware groups are targeting SharePoint customers across the globe.
By David Jones • July 24, 2025 -
Trump AI plan calls for cybersecurity assessments, threat info-sharing
It remains unclear how federal agencies depleted by layoffs will be able to implement the strategy’s ambitious vision, which includes an ISAC dedicated to AI.
By Eric Geller • July 23, 2025 -
SharePoint hacking campaign affects hundreds of systems worldwide
CISA is responding to potential compromises at federal agencies and various state and local entities.
By David Jones • Updated July 23, 2025 -
Microsoft sees China-backed nation-state hackers among adversaries targeting SharePoint
The company urged customers to apply security updates as security researchers warn of escalating attacks.
By David Jones • July 22, 2025 -
Microsoft, CISA warn of cyberattacks targeting on-premises SharePoint servers
The flaw has already led to widespread compromises prior to Microsoft’s release of an emergency patch.
By David Jones • Updated July 21, 2025 -
Top US senator calls out supply-chain risk with DoD contractors
The Senate Intelligence Committee chairman questioned the security of Microsoft’s “digital escort” arrangement with its Chinese employees.
By Eric Geller • Updated July 18, 2025 -
Researchers warn of cyberattacks targeting key Fortinet software
Experts urged Fortinet customers to immediately apply patches or disable the affected administrative interface.
By David Jones • Updated July 18, 2025