Threats
-
US authorities unmask North Korean IT worker schemes and their American accomplices
Federal officials said businesses should carefully verify the identities of remote employees to avoid falling prey to similar scams.
By Eric Geller • June 30, 2025 -
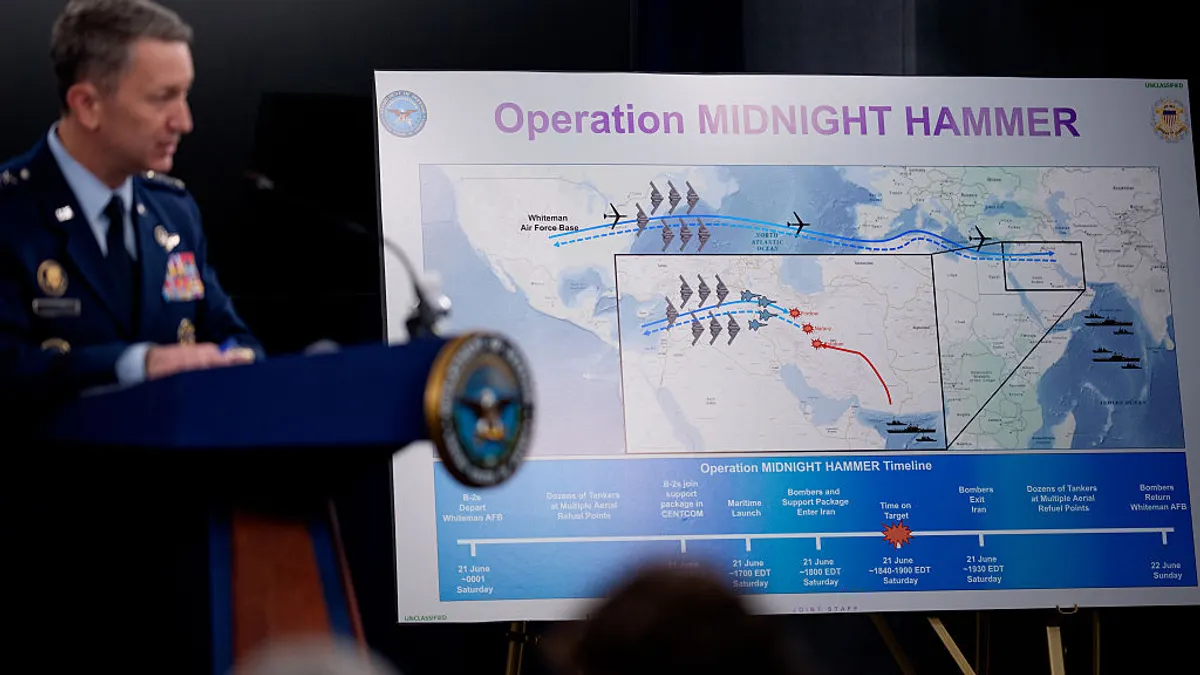
US government warns of new Iran-linked cyber threats on critical infrastructure
Companies should disconnect operational technology from the internet and enforce strong protections for user accounts, a joint alert from CISA, the FBI, NSA and DoD said.
By Eric Geller • June 30, 2025 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
Scattered Spider appears to pivot toward aviation sector
A cyberattack on Hawaiian Airlines carries some hallmarks of the notorious cybercrime group.
By David Jones • Updated June 27, 2025 -
Deep Dive
‘Suspended animation’: US government upheaval has frayed partnerships with critical infrastructure
Recent federal cuts, reorganizations and other disruptions have alarmed industry leaders, who say the government is a less reliable partner even as cyber threats increase.
By Eric Geller • June 25, 2025 -
Federal officials, critical infrastructure leaders remain on guard for Iran-linked hacks
Amid an uneasy truce, security teams in the U.S. said they have not seen any credible or specific threats.
By David Jones • June 24, 2025 -
Fewer ransomware attacks encrypting data, report finds
Hackers are increasingly performing extortion-only attacks.
By Eric Geller • June 24, 2025 -
DHS warns of heightened cyber threat as US enters Iran conflict
Federal officials are warning that pro-Iran hacktivists or state-linked actors may target poorly secured U.S. networks.
By David Jones • June 23, 2025 -
Aflac discloses cyber intrusion linked to wider crime spree targeting insurance industry
The breach marks the latest in a series of recent attacks linked to cybercrime group Scattered Spider.
By David Jones • Updated June 20, 2025 -
Cloud storage buckets leaking secret data despite security improvements
New data from Tenable highlighted significant improvements in the number of businesses with publicly exposed and critically vulnerable buckets storing sensitive data.
By Eric Geller • June 18, 2025 -
Threat group linked to UK, US retail attacks now targeting insurance industry
The warning from Google researchers follows a recent incident at Erie Insurance, although the perpetrators of that attack have not been identified.
By David Jones • June 16, 2025 -
US critical infrastructure could become casualty of Iran-Israel conflict
Researchers warn that Iran-aligned threat groups could soon target U.S. companies and individuals in cyber espionage or sabotage attacks.
By David Jones • June 16, 2025 -
Cyberattacks top list of global business concerns, Kroll finds
Many companies feel unprepared to comply with global privacy and security rules, according to the advisory firm’s annual business sentiment survey.
By Eric Geller • June 13, 2025 -
Global law-enforcement operation targets infostealer malware
Authorities in three countries arrested 32 people and seized dozens of servers.
By Eric Geller • June 11, 2025 -
Marks & Spencer restores some online-order operations following cyberattack
The department store chain six weeks ago was one of the first targets in an international spree of attacks disrupting retailers.
By David Jones • June 10, 2025 -
From malware to deepfakes, generative AI is transforming attacks
Generative AI is even helping hackers trick open-source developers into using malicious code, according to Gartner.
By Eric Geller • June 10, 2025 -
Scattered Spider targeting MSPs, IT vendors in social engineering campaigns
The same group is believed to be behind a wave of attacks against retailers in the UK, the US and elsewhere.
By David Jones • June 9, 2025 -
Data security is a CX issue, too
A string of cyberattacks have targeted retailers like Adidas and North Face. Incidents like these can weaken customer trust and lead to lost business, experts say.
By Kristen Doerer • June 9, 2025 -
SentinelOne rebuffs China-linked attack — and discovers global intrusions
The security firm said the operatives who tried to breach it turned out to be responsible for cyberattacks on dozens of critical infrastructure organizations worldwide.
By Eric Geller • Updated June 9, 2025 -
Main distributor to Whole Foods hit by cyberattack
UNFI, a grocery retailer and wholesaler, is working to resume full operations following “unauthorized activity” involving its IT systems.
By Sam Silverstein • June 9, 2025 -
Corporate executives face mounting digital threats as AI drives impersonation
Malicious actors are using deepfakes and voice-cloning technology to target senior executives in both the workplace and personal spaces.
By David Jones • June 6, 2025 -
FBI, CISA warn Play ransomware targeting critical infrastructure with evolving techniques
The hacker group has breached hundreds of organizations and is working with others to exploit flaws in a popular remote support tool.
By David Jones • June 5, 2025 -
Hackers abuse malicious version of Salesforce tool for data theft, extortion
A threat group is using voice phishing to trick targeted organizations into sharing sensitive credentials.
By David Jones • June 4, 2025 -
Victoria’s Secret postponing release of report earnings amid breach impact
The intrusion follows a string of attacks that appear to be the work of the cybercrime gang Scattered Spider.
By David Jones • June 3, 2025 -
Microsoft, CrowdStrike, other cyber firms collaborate on threat actor taxonomy
After years of confusion, leading threat-intelligence companies will streamline how they name threat groups.
By David Jones • June 2, 2025 -
ConnectWise warns of threat activity linked to suspected nation-state hackers
The company said suspicious activity has affected a limited number of ScreenConnect customers.
By David Jones • Updated May 30, 2025