Strategy
-
Scattered Spider poses serious risk to several hundred major companies
A new report shows that a select group of large companies uses technologies that the hacker group often targets.
By David Jones • July 8, 2025 -
Security coalition urges Congress to renew 2015 CISA law
A group of top cybersecurity and technology firms said the law provided critical protections for sharing essential vulnerability information.
By Eric Geller • July 8, 2025 -
 Explore the Trendline➔
Explore the Trendline➔
 .shock via Getty Images
.shock via Getty Images Trendline
TrendlineRisk Management
An esclation of cyber risks facing businesses and government has made cyber resilience a major priority.
By Cybersecurity Dive staff -
FBI cyber guidance to lawmakers falls short, US senator says
Sen. Ron Wyden wants FBI briefings to cover four often-overlooked cybersecurity practices.
By Eric Geller • July 2, 2025 -
US authorities unmask North Korean IT worker schemes and their American accomplices
Federal officials said businesses should carefully verify the identities of remote employees to avoid falling prey to similar scams.
By Eric Geller • June 30, 2025 -
US government warns of new Iran-linked cyber threats on critical infrastructure
Companies should disconnect operational technology from the internet and enforce strong protections for user accounts, a joint alert from CISA, the FBI, NSA and DoD said.
By Eric Geller • June 30, 2025 -
Most building management systems exposed to cyber vulnerabilities, experts warn
A study of over 467,000 building management systems across 500 organizations found that 2% of all devices essential to business operations had the highest level of risk exposure.
By Joe Burns • June 27, 2025 -
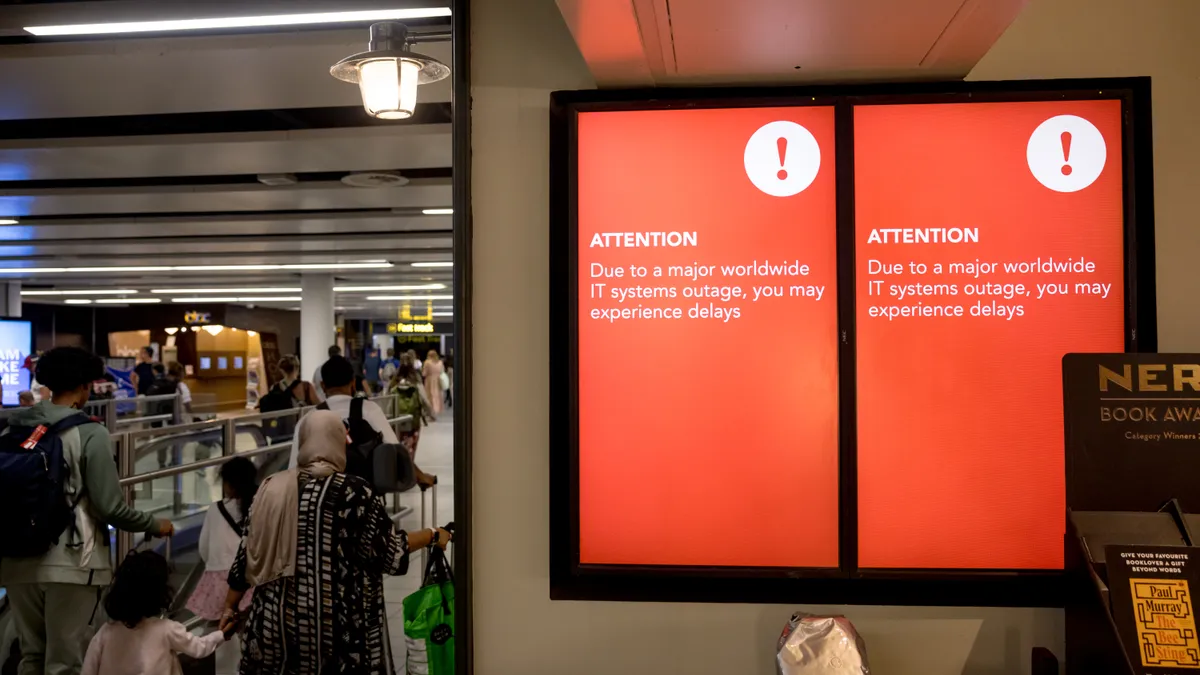
Microsoft to make Windows more resilient following 2024 IT outage
The company has been working with security partners to make sure future software updates don’t lead to operational disruptions for customers.
By David Jones • Updated June 26, 2025 -
AI security issues dominate corporate worries, spending
Two reports illustrate how business leaders are thinking about and budgeting for generative AI.
By Eric Geller • June 26, 2025 -
Judge approves AT&T’s $177M data breach settlement
The settlement, which has received preliminary clearance, now awaits a December hearing for final approval.
By Alexei Alexis • June 25, 2025 -
Deep Dive
‘Suspended animation’: US government upheaval has frayed partnerships with critical infrastructure
Recent federal cuts, reorganizations and other disruptions have alarmed industry leaders, who say the government is a less reliable partner even as cyber threats increase.
By Eric Geller • June 25, 2025 -
Federal officials, critical infrastructure leaders remain on guard for Iran-linked hacks
Amid an uneasy truce, security teams in the U.S. said they have not seen any credible or specific threats.
By David Jones • June 24, 2025 -
Cyber insurance premiums drop for first time, report finds
Despite a decline in both premiums and prices, the market continues to be profitable.
By Eric Geller • June 24, 2025 -
Businesses average 21 AI projects in production
Enterprises plan to expand their portfolios by the end of the year, according to a Rackspace Technology survey.
By Lindsey Wilkinson • June 23, 2025 -
DHS warns of heightened cyber threat as US enters Iran conflict
Federal officials are warning that pro-Iran hacktivists or state-linked actors may target poorly secured U.S. networks.
By David Jones • June 23, 2025 -
AWS CISO stumps for security as an AI enabler
AI’s rapid development underscores the need for secure foundations, Amy Herzog said Tuesday during the company’s annual cybersecurity conference.
By Roberto Torres • June 20, 2025 -
FTC reminds car dealers to protect customer data
The commission described how recently updated federal regulations affect dealerships — and their vendors.
By Eric Geller • Updated June 17, 2025 -
SEC scraps proposed cybersecurity rules for investment advisers, market participants
The commission offered no rationale for removing rules that would have imposed security requirements on financial services providers.
By Eric Geller • Updated June 16, 2025 -
US critical infrastructure could become casualty of Iran-Israel conflict
Researchers warn that Iran-aligned threat groups could soon target U.S. companies and individuals in cyber espionage or sabotage attacks.
By David Jones • June 16, 2025 -
Cyberattacks top list of global business concerns, Kroll finds
Many companies feel unprepared to comply with global privacy and security rules, according to the advisory firm’s annual business sentiment survey.
By Eric Geller • June 13, 2025 -
Software vulnerabilities pile up at government agencies, research finds
A Veracode report reveals that government networks have accumulated years of unresolved security flaws, putting them at serious risk of exploitation.
By David Jones • June 12, 2025 -
How AI agents could revolutionize the SOC — with human help
AI agents aren’t foolproof, but they could soon replace some of the most common tasks for cyber defenders.
By Eric Geller • June 11, 2025 -
Opinion
Gartner: How to create a compelling SOC narrative for executives
Focus on financial impact, efficiency and risk management to ensure informed cybersecurity investment decisions.
By Pete Shoard, VP analyst, Gartner Cybersecurity Threat Detection & Response • June 9, 2025 -
Trump scraps Biden software security, AI, post-quantum encryption efforts in new executive order
The White House accused the Biden administration of trying to “sneak problematic and distracting issues into cybersecurity policy.”
By Eric Geller • June 6, 2025 -
Trump’s national cyber director nominee dodges criticism of funding cuts
Sean Cairncross said his managerial experience has prepared him well to lead a relatively new White House cyber unit.
By Eric Geller • June 5, 2025 -
Banking groups urge SEC to rescind Biden-era cybersecurity rule
The rule has exposed companies to liability risks while failing to provide investors with “decision-useful” information, the coalition said in a recent letter.
By Alexei Alexis • June 5, 2025