Page 32
-
Xerox patches critical vulnerability in FreeFlow Core application
Researchers at Horizon3.ai discovered the flaw after flagging unusual behavior in a customer environment.
Updated Aug. 13, 2025 -
CISA, Microsoft update guidance on Exchange Server vulnerability
Officials reiterated their belief that hackers were not exploiting the flaw, but nonetheless urged users to immediately check their systems.
-
Financial impact from severe OT events could top $300B
A report from industrial cybersecurity firm Dragos highlights growing risks of business interruption and supply-chain disruptions.
-
Citrix NetScaler flaws lead to critical infrastructure breaches
Dutch authorities said hackers penetrated several critical infrastructure providers, in a warning sign for vulnerable organizations elsewhere.
Updated Aug. 12, 2025 -
DOJ, international partners take down BlackSuit group’s infrastructure
BlackSuit has been among the most prolific ransomware gangs in recent years, targeting government agencies, critical manufacturing companies and healthcare firms.
-
Research shows AI agents are highly vulnerable to hijacking attacks
Experts from Zenity Labs demonstrated how attackers could exploit widely deployed AI technologies for data theft and manipulation.
-
Cyber experts ponder a non-government future for the CVE program
Organizations supporting the security vulnerability program said it needed changes to improve stability and rebuild trust.
-
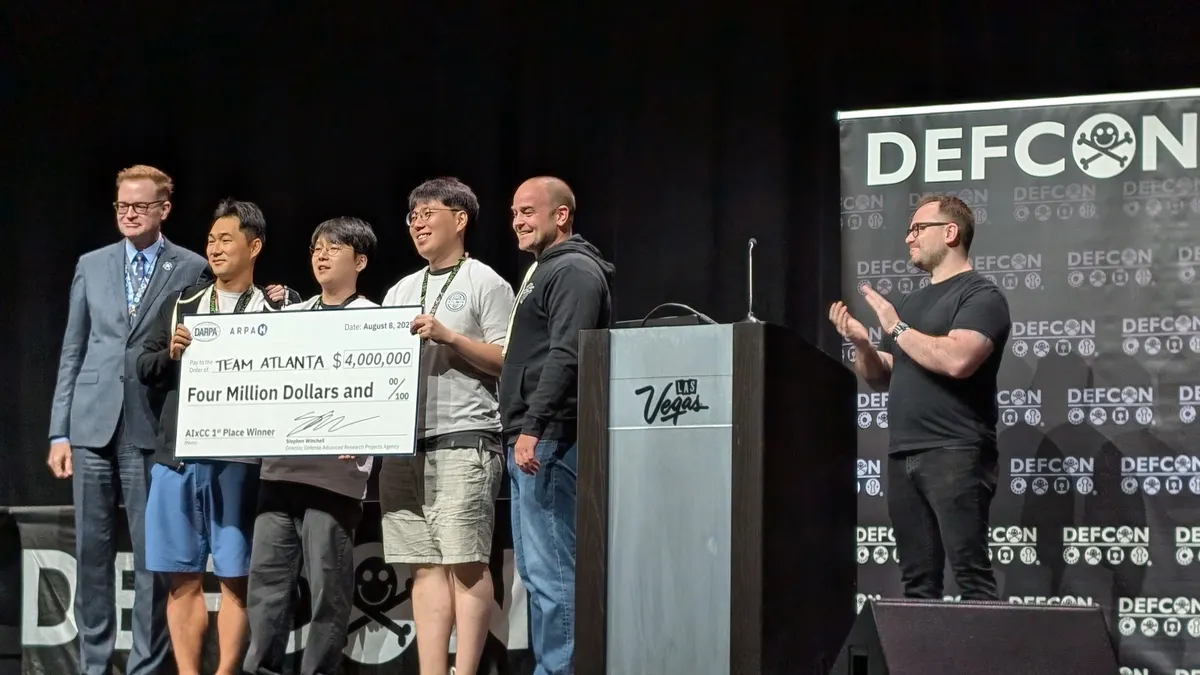
DARPA touts value of AI-powered vulnerability detection as it announces competition winners
The U.S. military research agency hopes to foster a new ecosystem of autonomous vulnerability remediation.
-
CISA officials say agency is moving ahead despite workforce purge
Two senior officials defended the agency’s progress amid concerns about the effects of mass layoffs and budget cuts.
-
Financially motivated cluster a key player in ToolShell exploitation
Researchers from Palo Alto Networks detail ransomware deployment and malicious backdoors in a campaign against Microsoft SharePoint users.
-
NSA partnering with cyber firms to support under-resourced defense contractors
The spy agency has sought out creative ways to help protect small companies supplying the U.S. military.
-
SonicWall says recent attack wave involved previously disclosed flaw, not zero-day
The company said it had linked recent hacks to customers’ use of legacy credentials when migrating from Gen 6 to Gen 7 firewalls.
-
CISA, Microsoft warn about new Microsoft Exchange server vulnerability
The flaw could enable a hacker to perform a “total domain compromise” on affected systems, CISA said.
Updated Aug. 7, 2025 -
US still prioritizing zero-trust migration to limit hacks’ damage
The zero-trust initiative, which gained steam during the Biden administration, is still underway.
Updated Aug. 7, 2025 -
CISA’s relationship with industry needs work to reestablish trust, experts say
Critics say budget cuts, job losses have hurt the agency’s ability to coordinate with private industry.
-
Top US energy companies frequently exposed to critical security flaws
A report from security firm SixMap shows that a large number of energy companies use equipment with vulnerabilities that are located on potentially exposed ports.
-
SonicWall investigating possible zero-day related to firewall attacks
Researchers recently warned about a surge in Akira ransomware attacks linked to a potential SonicWall vulnerability.
-
Cybersecurity budgets tighten as economic anxiety rises
Uncertain tariff policies and fluctuating inflation and interest rates are leading to stagnant or reduced budgets, according to an IANS Research report.
-
Senate confirms Trump’s national cyber director nominee
Sean Cairncross, a political veteran without significant cybersecurity experience, could turn the relatively new White House office into a major player in the administration.
-
AI is helping hackers automate and customize cyberattacks
CrowdStrike’s annual cyber-threat-hunting report reveals the double threat that AI poses to many businesses.
-
Ransomware spike linked to potential zero-day flaw in SonicWall devices
Researchers say hackers using the Akira ransomware strain may be exploiting the vulnerability en masse.
Updated Aug. 4, 2025 -
Palo Alto Networks investigating ransomware threat related to SharePoint exploitation
Researchers said an unidentified hacker demanded a ransom after an intrusion linked to the SharePoint flaw.
-
DOJ reaches $9.8 million settlement with Illumina over cyber whistleblower claims
The U.S. alleged the company knowingly sold genetic-sequencing systems with software vulnerabilities to federal agencies.
Updated Aug. 1, 2025 -
Industry groups urge vigilance as Scattered Spider evolves tactics
Information-sharing organizations warned their members that Scattered Spider continues to pose a major threat.
-
Ransomware gangs capitalize on law enforcement takedowns of competitors
After authorities dismantled LockBit and RansomHub, other groups rushed in to snatch up their affiliates, according to a new report that highlights a cybercrime ecosystem in flux.