Cyberattacks: Page 34
-
Ransomware attack surges tied to crypto spikes
Not every ransomware attempt leads to a successful attack. But with more attempts comes more potential damage.
By Matt Kapko • Aug. 24, 2022 -
Credential stuffing hammers US businesses as account data for sale in bulk
Media companies, retailers, restaurant groups and food delivery services are at heightened risk, the FBI said.
By Matt Kapko • Aug. 23, 2022 -
 Explore the Trendline➔
Explore the Trendline➔
 Getty Images
Getty Images
-
Third-party attacks spike as attackers target software connections
Every third-party tool and partnership is a potential path for attack and an opportunity to exploit human behavior. The risks spread far and wide.
By Matt Kapko • Aug. 22, 2022 -
LockBit ransomware group claims responsibility for Entrust attack
The prolific ransomware gang threatened to publish data stolen during the attack.
By Matt Kapko • Aug. 19, 2022 -
Mailchimp breach shines new light on digital identity, supply chain risk
Sophisticated threat actors are targeting weak links in the email marketing space to go after vulnerable financial targets.
By David Jones • Aug. 18, 2022 -
DigitalOcean, caught in Mailchimp security incident, drops email vendor
An attack on the email marketing firm raises questions about the continued risk of a supply chain compromise.
By David Jones • Aug. 17, 2022 -
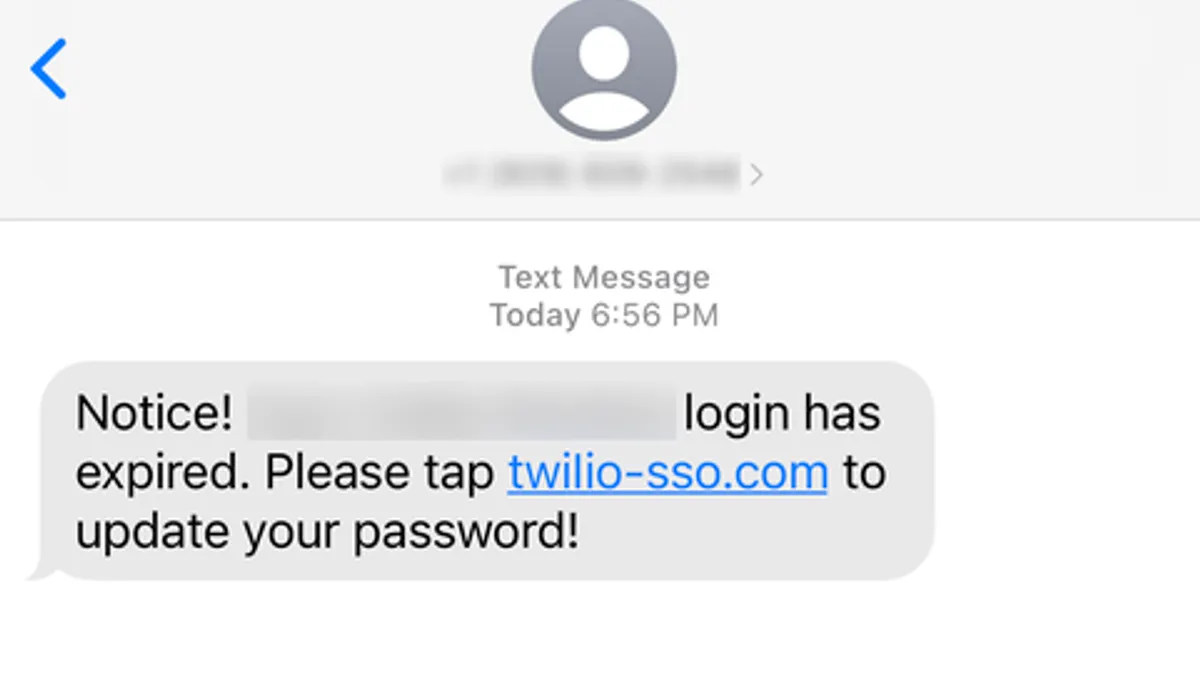
Twilio phishing attack fallout spreads to Signal
The vendor’s widely used two-factor authentication service became a point of potential compromise for 1,900 Signal users. One user suffered a direct hit.
By Matt Kapko • Aug. 15, 2022 -
How attackers are breaking into organizations
Threat actors lean heavily on phishing attacks, vulnerabilities in software and containers, and stolen credentials, according to top cyber vendor research.
By Matt Kapko • Aug. 15, 2022 -
Internal Cisco data stolen after employee hit by voice phishing attack
Cisco identified the attacker as an initial access broker with ties to multiple cybercrime and ransomware groups.
By Matt Kapko • Aug. 11, 2022 -
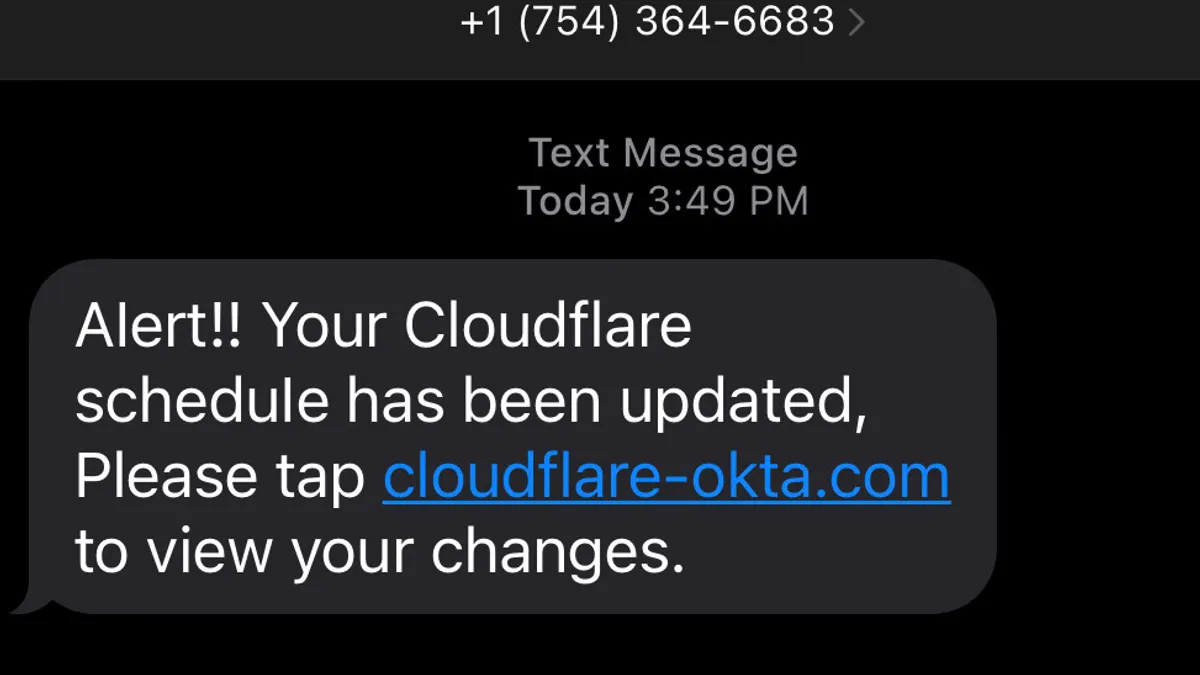
Cloudflare thwarts ‘sophisticated’ phishing attack strategy that bruised Twilio
Dissimilar responses from Cloudflare and Twilio bear important lessons in transparency, resiliency and access.
By Matt Kapko • Aug. 9, 2022 -
Twilio employees duped by text message phishing attack
The communications provider declined to say how many employees were duped and the amount of customers compromised.
By Matt Kapko • Aug. 8, 2022 -
Encevo stays resilient post-attack, but it’s still assessing the data damage
The Luxembourg energy supplier’s ability to thwart a shutdown likely empowered its refusal to pay a ransom.
By Matt Kapko • Aug. 8, 2022 -
The 11 most-prevalent malware strains of 2021 fuel cybercrime
Cybercriminals remain the most prolific users of malware, wielding these top strains to deliver ransomware and steal data.
By Matt Kapko • Aug. 5, 2022 -
Luxembourg energy supplier Encevo hit by ransomware attack
The group behind the attack threatened to leak more than 150 gigabytes of sensitive data on Monday.
By Matt Kapko • Aug. 1, 2022 -
Most cyberattacks come from ransomware, email compromise
Attackers are scanning for vulnerabilities in unpatched systems within 15 minutes, stressing the pace and scale of the threat.
By Matt Kapko • Aug. 1, 2022 -
Sponsored by Delinea
Benefits of modern PAM: Efficiency, security, compliance
Cloud-ready Privileged Access Management (PAM) is vital to your cyber defense strategy.
By Shweta Khare, Cybersecurity Evangelist, Delinea • Aug. 1, 2022 -
Entrust acknowledges June cyberattack, remains tight-lipped on the details
The cybersecurity vendor has yet to disclose how the incident occurred, the type of data stolen and if ransomware was involved.
By Matt Kapko • July 28, 2022 -
T-Mobile agrees to $500M settlement for 2021 cyberattack
The wireless carrier suffered a massive data breach in the summer of 2021, the fifth publicly acknowledged incident of its type in three years.
By Matt Kapko • July 25, 2022 -
LockBit ransomware hitting network servers
The latest tactic used to deploy the prolific malware allows threat actors to end processes, stop services and duplicate more quickly.
By Matt Kapko • July 20, 2022 -
Ransomware attacks surge in education sector
Colleges and universities are particularly challenged as repercussions of ransomware hit them harder and longer than other organizations.
By Matt Kapko • July 14, 2022 -
Threat actors favor brute force attacks to hit cloud services
Google Cloud warned that organizations face their greatest threat due to weak passwords and vulnerable software.
By Matt Kapko • July 12, 2022 -
Hospital ransomware concerns rise after payment vendor breach, North Korea threats
A recently disclosed ransomware attack could have exposed patient data from more than 650 healthcare providers.
By Rebecca Pifer Parduhn • July 11, 2022 -
Pricing pressures moderate as cyber insurance market begins to level out
A surge in new buyers has begun to offset years of rising claims and higher premiums, according to data from global insurance firm Marsh.
By Naomi Eide • July 1, 2022 -
Ransomware groups shift tactics and objectives
Malware can play a major or nonexistent role in ransomware attacks. Threat actors are often only in it for the money.
By Matt Kapko • June 15, 2022 -
How and why ransomware responses go haywire
A lack of fortitude and preparation on the communications front often puts enterprises at risk for greater harm.
By Matt Kapko • June 13, 2022